Forget about the desktop improvements and Bing smart search: Windows 8.1’s biggest draw may be the sheer volume of new and hidden features. Seriously—it’s jam-packed.
But apparently Microsoft needed to clear room for all the fresh ideas. Windows 8.1 shaves away many of Windows 8’s auxiliary features. Some of the removals are blatant once they’re pointed out, while others are more obscure, but all are off the table in Windows 8.1.
1. Messaging app
Windows 8’s IM capabilities were handled by the aptly named Messaging, one of the core apps shining front and center on the live-tiled Start screen. No more: Microsoft has kicked Messaging to the curb less than a year after the app’s arrival, replacing the Windows 8 native with Skype.
As high-profile as the swap is, it’s no great loss. Messaging was pretty lackluster and largely overlapped Skype’s core functionality. Meanwhile, Skype’s Communication services are also being baked into the Xbox One and Outlook.com (but not Windows Phone). One bummer: Messaging supported Facebook Chat, while Skype does not.
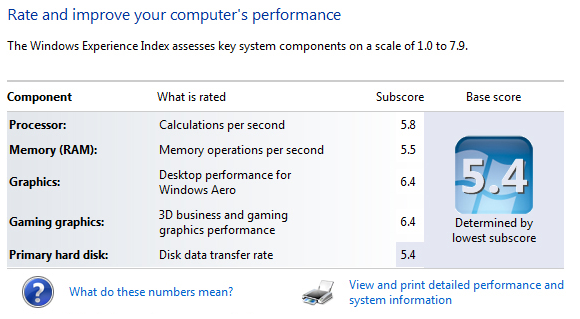
2. Windows Experience Index
Ever since the Vista days, Windows provided a “Windows Experience Index” score in your My Computer properties. The WEI score was supposed to be a numerical indicator of your PC’s brawn. Powerful PCs received higher scores, and so on.
Unfortunately, the WEI’s scoring criteria weren’t well known, and it placed odd, seemingly artificial caps on the highest possible scores. (Windows 7’s cap was 7.9, while Vista’s was 5.9.) Whether for these or other reasons, the WEI never seemed to catch on, and it’s nowhere to be found in Windows 8.1.
3. Facebook and Flickr in the Photos app
Regrettably, Windows 8.1’s Photos app no longer supports Facebook and Flickr image integration.
“In Windows 8, we wanted to provide a way for folks to view their photos on other services, knowing there would be few (if any) apps in the store at launch that would do so,” a Microsoft representative said. “Now there are many apps in the store that offer ways to view photos on other services.”
A Facebook app launched in the Windows Store the same day as Windows 8.1, but its image-management and sharing capabilities aren’t as flexible as those in Windows 8’s Photos app. And despite Flickr’s sudden disappearance from the Photos app, an official app for that service has yet to appear in the Windows Store.
4. Libraries?
Your Documents, Music, Pictures, and Videos libraries aren’t visible by default in Windows 8.1—but that doesn’t mean they’re not there. Activating them is easy, as shown in the single screenshot below.
Some websites are reporting, though, that Windows 8.1’s libraries ditch Public Folders. Our experiences are a bit more hit-and-miss: Public folders appeared in my Windows 8.1 libraries after I upgraded from Windows 8, but they were a no-show in the libraries of another PCWorld editor.
Don’t let that bring you down! After reenabling libraries using the method outlined above, just right-click a library and select Properties > Add… to toss additional folders into the mix.
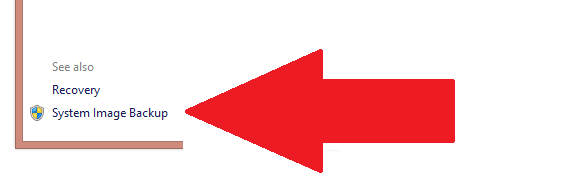
5. Windows 7 File Recovery, kind of
Ominous portents swirled when the Windows 8.1 Preview pushed out without the ‘Windows 7 File Recovery’ image-backup option found in Windows 8, especially since Microsoft has clearly stated that the tool is being deprecated in favor of Windows 8’s File History. And yes, it’s still missing in Windows 8.1.
But fear not! Though Windows 7 File Recovery is dead in name, it lives on in spirit as ‘System Image Backup’. Just head to Control Panel > System & Security > File History, and then look in the lower-left corner.
6. Apps splashed on the Start screen
In Windows 8, all newly installed apps and desktop programs automatically received a tile on the modern Start screen. That isn’t the case in Windows 8.1: Now, you have to dive into the All Apps screen and manually pin new software to the Start screen.
That’s a big win in my book, since installing desktop programs often plopped tiles for dozens of auxiliary executables, languages, and other options on the Start screen alongside the link to the base program, resulting in a distressing amount of clutter. Less-seasoned computer users may become confused when installed apps fail to appear on the Start screen by default, however—especially since the returned Start button’s behavior trains you to consider the Start screen as a “modern”-day Start-menu replacement. Steel yourself for the support calls from family and friends.
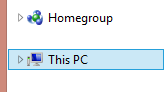
7. My Computer
Yes, the nearly 20-year-old ‘My Computer’ moniker has retired, giving way to the more cloud- and cross-platform-friendly ‘This PC’. Desktop fallout from the focus on “One Microsoft” continues—though this is an admittedly trivial change.
8. SkyDrive desktop program
Keen-eyed SkyDrive users will note that jumping to Windows 8.1 erases the discrete (and optional) SkyDrive desktop software that served to keep local files in sync with the cloud. And that makes sense: Microsoft’s cloud service weaves itself tightly into Windows 8.1, and the desktop program’s functionality has largely been replaced by the update’s native SkyDrive support.
9. SkyDrive desktop-program functionality
Continuing with that theme, some of the more obscure yet helpful functions of the SkyDrive desktop program haven’t been replicated by Windows 8.1’s native features. For one thing, upgrading to Windows 8.1 kills SkyDrive’s remote Fetch feature.
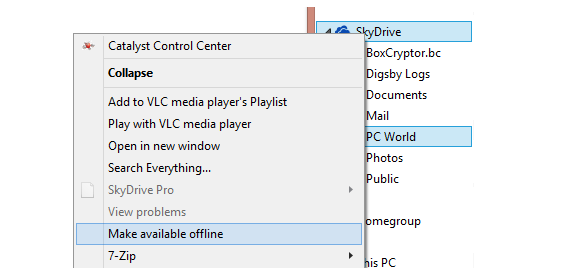
Also be aware that unlike the desktop program, SkyDrive in Windows 8.1 relies on symbolic links to point to cloud-stored files in File Explorer, even though everything appears to be saved locally at first glance. This “smart files” functionality can save a lot of space on tablets and other storage-restricted devices, but if you’d like to keep local copies of your stuff, right-click the SkyDrive icon in File Explorer and select Make available offline.
You can also right-click individual files and folders and choose to make them online-only or available offline.
Still worth the upgrade
Don’t let these little omissions dissuade you: Windows 8.1 is superior to Windows 8 in virtually every way. It represents a much less jarring version of Microsoft’s grand vision of a cross-platform future—though it still won’t win over folks whose lips instinctively curl at the merest mention of the word “Metro.” Check out PCWorld’s definitive review of Windows 8.1for all the juicy details. (And if you’re one of those desktop diehards, you might want to check out our guide to banishing the modern UI from your Windows 8.1 PC.)